Imagine that you need to load test a Network Management System (NMS), which might receive hundreds of SNMP traps every second from tens of thousands of devices on the network. Clearly it is impractical to actually deploy thousands of devices in a test environment, so you need a tool to generate the SNMP traps at the required volume.
A quick search for SNMP load testing tools shows that they are all fairly primitive, with poor support for creating SNMP traps with dynamic field values, and no support for integrated system monitoring. There are definitely no tools with the same level of functionality as LoadRunner.
Unfortunately LoadRunner does not have an SNMP vuser type…but fortunately LoadRunner is endlessly extensible, if you are not afraid to get your hands dirty. Read on for how I created a LoadRunner script to send SNMP traps to an NMS…
The first step was to capture some SNMP traps. This is best done by packet capture on the NMS server. Here is an example SNMP trap, displayed in Wireshark:
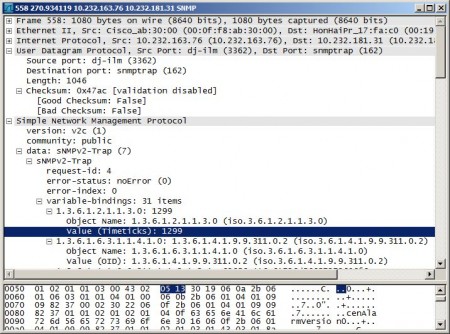
This example SNMP trap is from Cisco Enterprise Policy Manager (CW_LMS_CISCO-EPM-NOTIFICATION-MIB.mib).
The SNMP trap can be dumped out to a less friendly, but more useful format (format is Offest, Hex, Text):
0000 30 82 04 0a 02 01 01 04 06 70 75 62 6c 69 63 a7 0........public.
0010 82 03 fb 02 01 04 02 01 00 02 01 00 30 82 03 ee ............0...
0020 30 0e 06 08 2b 06 01 02 01 01 03 00 43 02 05 13 0...+.......C...
0030 30 19 06 0a 2b 06 01 06 03 01 01 04 01 00 06 0b 0...+...........
0040 2b 06 01 04 01 09 09 82 37 00 02 30 22 06 0f 2b +.......7..0"..+
0050 06 01 04 01 09 09 82 37 01 01 02 01 02 01 04 0f .......7........
0060 63 65 6e 41 6c 61 72 6d 56 65 72 73 69 6f 6e 30 cenAlarmVersion0
0070 16 06 0f 2b 06 01 04 01 09 09 82 37 01 01 02 01 ...+.......7....
0080 03 01 43 03 01 8a 92 30 16 06 0f 2b 06 01 04 01 ..C....0...+....
0090 09 09 82 37 01 01 02 01 04 01 43 03 01 8a 92 30 ...7......C....0
00a0 25 06 0f 2b 06 01 04 01 09 09 82 37 01 01 02 01 %..+.......7....
00b0 05 01 04 12 63 65 6e 41 6c 61 72 6d 49 6e 73 74 ....cenAlarmInst
00c0 61 6e 63 65 49 44 30 14 06 0f 2b 06 01 04 01 09 anceID0...+.....
00d0 09 82 37 01 01 02 01 06 01 02 01 01 30 2b 06 0f ..7.........0+..
00e0 2b 06 01 04 01 09 09 82 37 01 01 02 01 07 01 04 +.......7.......
00f0 18 63 65 6e 41 6c 61 72 6d 53 74 61 74 75 73 44 .cenAlarmStatusD
0100 65 66 69 6e 69 74 69 6f 6e 30 14 06 0f 2b 06 01 efinition0...+..
0110 04 01 09 09 82 37 01 01 02 01 08 01 02 01 01 30 .....7.........0
0120 14 06 0f 2b 06 01 04 01 09 09 82 37 01 01 02 01 ...+.......7....
0130 09 01 02 01 00 30 2d 06 0f 2b 06 01 04 01 09 09 .....0-..+......
0140 82 37 01 01 02 01 0a 01 04 1a 63 65 6e 41 6c 61 .7........cenAla
0150 72 6d 43 61 74 65 67 6f 72 79 44 65 66 69 6e 69 rmCategoryDefini
0160 74 69 6f 6e 30 14 06 0f 2b 06 01 04 01 09 09 82 tion0...+.......
0170 37 01 01 02 01 0b 01 02 01 00 30 28 06 0f 2b 06 7.........0(..+.
0180 01 04 01 09 09 82 37 01 01 02 01 0c 01 04 15 63 ......7........c
0190 65 6e 41 6c 61 72 6d 53 65 72 76 65 72 41 64 64 enAlarmServerAdd
01a0 72 65 73 73 30 2e 06 0f 2b 06 01 04 01 09 09 82 ress0...+.......
01b0 37 01 01 02 01 0d 01 04 1b 63 65 6e 41 6c 61 72 7........cenAlar
01c0 6d 4d 61 6e 61 67 65 64 4f 62 6a 65 63 74 43 6c mManagedObjectCl
01d0 61 73 73 31 30 14 06 0f 2b 06 01 04 01 09 09 82 ass10...+.......
01e0 37 01 01 02 01 0e 01 02 01 00 30 21 06 0f 2b 06 7.........0!..+.
01f0 01 04 01 09 09 82 37 01 01 02 01 0f 01 04 0e 31 ......7........1
0200 30 2e 32 33 32 2e 31 38 30 2e 31 30 31 30 46 06 0.232.180.1010F.
0210 0f 2b 06 01 04 01 09 09 82 37 01 01 02 01 10 01 .+.......7......
0220 04 33 58 58 58 3a 43 6f 6d 70 6f 6e 65 6e 74 3d .3XXX:Component=
0230 43 6f 6d 70 6f 6e 65 6e 74 31 3b 43 6f 6d 70 6f Component1;Compo
0240 6e 65 6e 74 43 6c 61 73 73 2d 43 43 6c 61 73 73 nentClass-CClass
0250 31 3b 59 59 59 30 14 06 0f 2b 06 01 04 01 09 09 1;YYY0...+......
0260 82 37 01 01 02 01 11 01 02 01 02 30 2d 06 0f 2b .7.........0-..+
0270 06 01 04 01 09 09 82 37 01 01 02 01 12 01 04 1a .......7........
0280 63 65 6e 41 6c 61 72 6d 53 65 76 65 72 69 74 79 cenAlarmSeverity
0290 44 65 66 69 6e 69 74 69 6f 6e 30 14 06 0f 2b 06 Definition0...+.
02a0 01 04 01 09 09 82 37 01 01 02 01 13 01 02 01 01 ......7.........
02b0 30 17 06 0f 2b 06 01 04 01 09 09 82 37 01 01 02 0...+.......7...
02c0 01 14 01 04 04 31 30 30 30 30 22 06 0f 2b 06 01 .....10000"..+..
02d0 04 01 09 09 82 37 01 01 02 01 15 01 04 0f 63 65 .....7........ce
02e0 6e 55 73 65 72 4d 65 73 73 61 67 65 31 30 22 06 nUserMessage10".
02f0 0f 2b 06 01 04 01 09 09 82 37 01 01 02 01 16 01 .+.......7......
0300 04 0f 63 65 6e 55 73 65 72 4d 65 73 73 61 67 65 ..cenUserMessage
0310 32 30 22 06 0f 2b 06 01 04 01 09 09 82 37 01 01 20"..+.......7..
0320 02 01 17 01 04 0f 63 65 6e 55 73 65 72 4d 65 73 ......cenUserMes
0330 73 61 67 65 33 30 14 06 0f 2b 06 01 04 01 09 09 sage30...+......
0340 82 37 01 01 02 01 18 01 02 01 02 30 14 06 0f 2b .7.........0...+
0350 06 01 04 01 09 09 82 37 01 01 02 01 19 01 42 01 .......7......B.
0360 01 30 23 06 0f 2b 06 01 04 01 09 09 82 37 01 01 .0#..+.......7..
0370 02 01 1a 01 04 10 63 65 6e 50 61 72 74 69 74 69 ......cenPartiti
0380 6f 6e 4e 61 6d 65 30 2c 06 0f 2b 06 01 04 01 09 onName0,..+.....
0390 09 82 37 01 01 02 01 1b 01 04 19 63 65 6e 43 75 ..7........cenCu
03a0 73 74 6f 6d 65 72 49 64 65 6e 74 69 66 69 63 61 stomerIdentifica
03b0 74 69 6f 6e 30 26 06 0f 2b 06 01 04 01 09 09 82 tion0&..+.......
03c0 37 01 01 02 01 1c 01 04 13 63 65 6e 43 75 73 74 7........cenCust
03d0 6f 6d 65 72 52 65 76 69 73 69 6f 6e 30 1d 06 0f omerRevision0...
03e0 2b 06 01 04 01 09 09 82 37 01 01 02 01 1d 01 04 +.......7.......
03f0 0a 63 65 6e 41 6c 65 72 74 49 44 30 11 06 09 2b .cenAlertID0...+
0400 06 01 06 03 12 01 03 00 40 04 7f 00 ........@...
In theory, we can take the hex values from the above SNMP message, and send the same data using a Windows Sockets vuser.
/*********************************************************************
* Created by Mercury Interactive Windows Sockets Recorder
* Author: Stuart Moncrieff (www.myloadtest.com)
*********************************************************************/
#include "lrs.h"
vuser_init()
{
lrs_startup(257); // The lrs_startup function initializes the Windows Sockets DLL. It specifies the highest Windows Sockets version that can be used with the application.
// Note that UDP is "connectionless", so the message will still be sent, even if the IP address does not exist.
lrs_create_socket("socket0", "UDP", "LocalHost=0", "RemoteHost=10.232.181.31:162", LrsLastArg);
return 0;
}
Action()
{
/*
Send an SNMP trap. Note that there will be no response, so there
is no lrs_receive(), and there is nothing to verify, so this transaction always passes.
The transaction has been defined only so that the number of SNMP traps can be counted.
The data that is sent (buf0) can be found in the data.ws file.
*/
lr_start_transaction("send_snmp_trap");
lrs_send("socket0", "buf0", LrsLastArg);
lr_end_transaction("send_snmp_trap", LR_AUTO);
return 0;
}
vuser_end()
{
lrs_cleanup(); // Terminates the use of the WinSock DLL.
return 0;
}
// Here is the contents of the data.ws file.
;WSRData 2 1
// Once input values are parameterised, the size of the buffer may need to change (not sure how to handle dynamic sizing).
// To decode the hex values, just replay the script with full logging and look at the Replay Log.
// Note that VuGen throws an error if comments appear next to the constant strings in the buffer.
// Buffer size: 16 columns x 65 rows - 4 bytes = 1040 - 4 = 1036 bytes
send buf0 625
"\x30\x82\x04\x0a\x02\x01\x01\x04\x06\x70\x75\x62\x6c\x69\x63\xa7"
"\x82\x03\xfb\x02\x01\x04\x02\x01\x00\x02\x01\x00\x30\x82\x03\xee"
"\x30\x0e\x06\x08\x2b\x06\x01\x02\x01\x01\x03\x00\x43\x02\x05\x13"
"\x30\x19\x06\x0a\x2b\x06\x01\x06\x03\x01\x01\x04\x01\x00\x06\x0b"
"\x2b\x06\x01\x04\x01\x09\x09\x82\x37\x00\x02\x30\x22\x06\x0f\x2b"
"\x06\x01\x04\x01\x09\x09\x82\x37\x01\x01\x02\x01\x02\x01\x04\x0f"
"\x63\x65\x6e\x41\x6c\x61\x72\x6d\x56\x65\x72\x73\x69\x6f\x6e\x30"
"\x16\x06\x0f\x2b\x06\x01\x04\x01\x09\x09\x82\x37\x01\x01\x02\x01"
"\x03\x01\x43\x03\x01\x8a\x92\x30\x16\x06\x0f\x2b\x06\x01\x04\x01"
"\x09\x09\x82\x37\x01\x01\x02\x01\x04\x01\x43\x03\x01\x8a\x92\x30"
"\x25\x06\x0f\x2b\x06\x01\x04\x01\x09\x09\x82\x37\x01\x01\x02\x01"
"\x05\x01\x04\x12\x63\x65\x6e\x41\x6c\x61\x72\x6d\x49\x6e\x73\x74"
"\x61\x6e\x63\x65\x49\x44\x30\x14\x06\x0f\x2b\x06\x01\x04\x01\x09"
"\x09\x82\x37\x01\x01\x02\x01\x06\x01\x02\x01\x01\x30\x2b\x06\x0f"
"\x2b\x06\x01\x04\x01\x09\x09\x82\x37\x01\x01\x02\x01\x07\x01\x04"
"\x18\x63\x65\x6e\x41\x6c\x61\x72\x6d\x53\x74\x61\x74\x75\x73\x44"
"\x65\x66\x69\x6e\x69\x74\x69\x6f\x6e\x30\x14\x06\x0f\x2b\x06\x01"
"\x04\x01\x09\x09\x82\x37\x01\x01\x02\x01\x08\x01\x02\x01\x01\x30"
"\x14\x06\x0f\x2b\x06\x01\x04\x01\x09\x09\x82\x37\x01\x01\x02\x01"
"\x09\x01\x02\x01\x00\x30\x2d\x06\x0f\x2b\x06\x01\x04\x01\x09\x09"
"\x82\x37\x01\x01\x02\x01\x0a\x01\x04\x1a\x63\x65\x6e\x41\x6c\x61"
"\x72\x6d\x43\x61\x74\x65\x67\x6f\x72\x79\x44\x65\x66\x69\x6e\x69"
"\x74\x69\x6f\x6e\x30\x14\x06\x0f\x2b\x06\x01\x04\x01\x09\x09\x82"
"\x37\x01\x01\x02\x01\x0b\x01\x02\x01\x00\x30\x28\x06\x0f\x2b\x06"
"\x01\x04\x01\x09\x09\x82\x37\x01\x01\x02\x01\x0c\x01\x04\x15\x63"
"\x65\x6e\x41\x6c\x61\x72\x6d\x53\x65\x72\x76\x65\x72\x41\x64\x64"
"\x72\x65\x73\x73\x30\x2e\x06\x0f\x2b\x06\x01\x04\x01\x09\x09\x82"
"\x37\x01\x01\x02\x01\x0d\x01\x04\x1b\x63\x65\x6e\x41\x6c\x61\x72"
"\x6d\x4d\x61\x6e\x61\x67\x65\x64\x4f\x62\x6a\x65\x63\x74\x43\x6c"
"\x61\x73\x73\x31\x30\x14\x06\x0f\x2b\x06\x01\x04\x01\x09\x09\x82"
"\x37\x01\x01\x02\x01\x0e\x01\x02\x01\x00\x30\x21\x06\x0f\x2b\x06"
"\x01\x04\x01\x09\x09\x82\x37\x01\x01\x02\x01\x0f\x01\x04\x0e\x31"
"\x30\x2e\x32\x33\x32\x2e\x31\x38\x30\x2e\x31\x30\x31\x30\x46\x06"
"\x0f\x2b\x06\x01\x04\x01\x09\x09\x82\x37\x01\x01\x02\x01\x10\x01"
"\x04\x33\x58\x58\x58\x3a\x43\x6f\x6d\x70\x6f\x6e\x65\x6e\x74\x3d"
"\x43\x6f\x6d\x70\x6f\x6e\x65\x6e\x74\x31\x3b\x43\x6f\x6d\x70\x6f"
"\x6e\x65\x6e\x74\x43\x6c\x61\x73\x73\x2d\x43\x43\x6c\x61\x73\x73"
"\x31\x3b\x59\x59\x59\x30\x14\x06\x0f\x2b\x06\x01\x04\x01\x09\x09"
"\x82\x37\x01\x01\x02\x01\x11\x01\x02\x01\x02\x30\x2d\x06\x0f\x2b"
"\x06\x01\x04\x01\x09\x09\x82\x37\x01\x01\x02\x01\x12\x01\x04\x1a"
"\x63\x65\x6e\x41\x6c\x61\x72\x6d\x53\x65\x76\x65\x72\x69\x74\x79"
"\x44\x65\x66\x69\x6e\x69\x74\x69\x6f\x6e\x30\x14\x06\x0f\x2b\x06"
"\x01\x04\x01\x09\x09\x82\x37\x01\x01\x02\x01\x13\x01\x02\x01\x01"
"\x30\x17\x06\x0f\x2b\x06\x01\x04\x01\x09\x09\x82\x37\x01\x01\x02"
"\x01\x14\x01\x04\x04\x31\x30\x30\x30\x30\x22\x06\x0f\x2b\x06\x01"
"\x04\x01\x09\x09\x82\x37\x01\x01\x02\x01\x15\x01\x04\x0f\x63\x65"
"\x6e\x55\x73\x65\x72\x4d\x65\x73\x73\x61\x67\x65\x31\x30\x22\x06"
"\x0f\x2b\x06\x01\x04\x01\x09\x09\x82\x37\x01\x01\x02\x01\x16\x01"
"\x04\x0f\x63\x65\x6e\x55\x73\x65\x72\x4d\x65\x73\x73\x61\x67\x65"
"\x32\x30\x22\x06\x0f\x2b\x06\x01\x04\x01\x09\x09\x82\x37\x01\x01"
"\x02\x01\x17\x01\x04\x0f\x63\x65\x6e\x55\x73\x65\x72\x4d\x65\x73"
"\x73\x61\x67\x65\x33\x30\x14\x06\x0f\x2b\x06\x01\x04\x01\x09\x09"
"\x82\x37\x01\x01\x02\x01\x18\x01\x02\x01\x02\x30\x14\x06\x0f\x2b"
"\x06\x01\x04\x01\x09\x09\x82\x37\x01\x01\x02\x01\x19\x01\x42\x01"
"\x01\x30\x23\x06\x0f\x2b\x06\x01\x04\x01\x09\x09\x82\x37\x01\x01"
"\x02\x01\x1a\x01\x04\x10\x63\x65\x6e\x50\x61\x72\x74\x69\x74\x69"
"\x6f\x6e\x4e\x61\x6d\x65\x30\x2c\x06\x0f\x2b\x06\x01\x04\x01\x09"
"\x09\x82\x37\x01\x01\x02\x01\x1b\x01\x04\x19\x63\x65\x6e\x43\x75"
"\x73\x74\x6f\x6d\x65\x72\x49\x64\x65\x6e\x74\x69\x66\x69\x63\x61"
"\x74\x69\x6f\x6e\x30\x26\x06\x0f\x2b\x06\x01\x04\x01\x09\x09\x82"
"\x37\x01\x01\x02\x01\x1c\x01\x04\x13\x63\x65\x6e\x43\x75\x73\x74"
"\x6f\x6d\x65\x72\x52\x65\x76\x69\x73\x69\x6f\x6e\x30\x1d\x06\x0f"
"\x2b\x06\x01\x04\x01\x09\x09\x82\x37\x01\x01\x02\x01\x1d\x01\x04"
"\x0a\x63\x65\x6e\x41\x6c\x65\x72\x74\x49\x44\x30\x11\x06\x09\x2b"
"\x06\x01\x06\x03\x12\x01\x03\x00\x40\x04\x7f\x00"
-1
But theory doesn’t quite match reality. Wireshark identifies this as UDP data, instead of an SNMP trap. If anyone can explain this, I would love to hear from them.
Plan B is to use a Java vuser (instead of the Winsock vuser), and write some simple Java code that will send the SNMP trap. Here is the code:
/*
* This LoadRunner script will send an SNMP trap.
*
* It can be used with either the Java vuser type (available in the Templates bundle),
* or with the Java Record-Replay vuser type (available in the Java Record/Replay bundle).
* Both bundles cost the same, so pick the one that is most useful for your other projects.
*
*
* NOTES
*
* This script requires snmp4j-1.11.3.jar, which is available from http://www.snmp4j.org/
* JavaDocs: http://www.snmp4j.org/doc/index.html
* This script should be threadsafe, so you can run it as a process or a thread in the Runtime Settings.
*/
import lrapi.lr; // LoadRunner methods (lr.start_transaction(), etc.)
import org.snmp4j.*; // Provides classes and interfaces for creating, sending, and receiving SNMP messages.
import org.snmp4j.smi.*; // Provides classes for the representation of SMIv1/v2 data types.
import org.snmp4j.mp.*; // Provides classes and interfaces for the SNMP message processing.
import org.snmp4j.transport.*; // Provides transport protocol mappings for SNMP.
public class Actions
{
public int init() throws Throwable {
// Ignore this method.
return 0;
}//end of init
public int action() throws Throwable {
OID oid; // SNMP Object ID
Variable var; // A Variable object can hold any of the SNMP variable types (e.g. OctetString, Integer32, Gauge32, TimeTicks,etc).
// Create an SNMP Protocol Data Unit.
PDU trap = new PDU();
trap.setType(PDU.TRAP);
// Create the OIDs and their values.
// Variable Bindings: 31 Items
// 1. SNMPv2-MIB::sysUpTime.0 (1.3.6.1.2.1.1.3.0): 1299
trap.add(new VariableBinding(SnmpConstants.sysUpTime, new TimeTicks(1299)));
// 2. SNMPv2-MIB::snmpTrapOID.0 (1.3.6.1.6.3.1.1.4.1.0): 1.3.6.1.4.1.9.9.311.0.2 (SNMPv2-SMI::enterprises.9.9.311.0.2)
oid = new OID("1.3.6.1.4.1.9.9.311.0.2");
trap.add(new VariableBinding(SnmpConstants.snmpTrapOID, oid));
// 3. 1.3.6.1.4.1.9.9.311.1.1.2.1.2.1: 63656e416c61726d56657273696f6e
oid = new OID("1.3.6.1.4.1.9.9.311.1.1.2.1.2.1");
var = new OctetString("cenAlarmVersion");
trap.add(new VariableBinding(oid, var));
// 4. 1.3.6.1.4.1.9.9.311.1.1.2.1.3.1: 101010
oid = new OID("1.3.6.1.4.1.9.9.311.1.1.2.1.3.1");
var = new TimeTicks(101010);
trap.add(new VariableBinding(oid, var));
// 5. 1.3.6.1.4.1.9.9.311.1.1.2.1.4.1: 101010
oid = new OID("1.3.6.1.4.1.9.9.311.1.1.2.1.4.1");
var = new TimeTicks(101010);
trap.add(new VariableBinding(oid, var));
// 6. 1.3.6.1.4.1.9.9.311.1.1.2.1.5.1: 63656e416c61726d496e7374616e63654944
oid = new OID("1.3.6.1.4.1.9.9.311.1.1.2.1.5.1");
var = new OctetString("cenAlarmInstanceId");
trap.add(new VariableBinding(oid, var));
// 7. 1.3.6.1.4.1.9.9.311.1.1.2.1.6.1:
oid = new OID("1.3.6.1.4.1.9.9.311.1.1.2.1.6.1");
var = new Integer32(1);
trap.add(new VariableBinding(oid, var));
// 8. 1.3.6.1.4.1.9.9.311.1.1.2.1.7.1: 63656e416c61726d537461747573446566696e6974696f6e
oid = new OID("1.3.6.1.4.1.9.9.311.1.1.2.1.7.1");
var = new OctetString("cenAlarmStatusDefinition");
trap.add(new VariableBinding(oid, var));
// 9. 1.3.6.1.4.1.9.9.311.1.1.2.1.8.1:
oid = new OID("1.3.6.1.4.1.9.9.311.1.1.2.1.8.1");
var = new Integer32(1);
trap.add(new VariableBinding(oid, var));
// 10. 1.3.6.1.4.1.9.9.311.1.1.2.1.9.1:
oid = new OID("1.3.6.1.4.1.9.9.311.1.1.2.1.9.1");
var = new Integer32(0);
trap.add(new VariableBinding(oid, var));
// 11. 1.3.6.1.4.1.9.9.311.1.1.2.1.10.1: 63656e416c61726d43617465676f7279446566696e697469...
oid = new OID("1.3.6.1.4.1.9.9.311.1.1.2.1.10.1");
var = new OctetString("cenAlarmCategoryDefinition");
trap.add(new VariableBinding(oid, var));
// 12. 1.3.6.1.4.1.9.9.311.1.1.2.1.11.1:
oid = new OID("1.3.6.1.4.1.9.9.311.1.1.2.1.11.1");
var = new Integer32(0);
trap.add(new VariableBinding(oid, var));
// 13. 1.3.6.1.4.1.9.9.311.1.1.2.1.12.1: 63656e416c61726d53657276657241646472657373
oid = new OID("1.3.6.1.4.1.9.9.311.1.1.2.1.12.1");
var = new OctetString("cenAlarmServerAddress");
trap.add(new VariableBinding(oid, var));
// 14. 1.3.6.1.4.1.9.9.311.1.1.2.1.13.1: 63656e416c61726d4d616e616765644f626a656374436c61...
oid = new OID("1.3.6.1.4.1.9.9.311.1.1.2.1.13.1");
var = new OctetString("cenAlarmManagedObjectClass");
trap.add(new VariableBinding(oid, var));
// 15. 1.3.6.1.4.1.9.9.311.1.1.2.1.14.1:
oid = new OID("1.3.6.1.4.1.9.9.311.1.1.2.1.14.1");
var = new Integer32(0);
trap.add(new VariableBinding(oid, var));
// 16. 1.3.6.1.4.1.9.9.311.1.1.2.1.15.1: 31302e3233322e3138302e313031
oid = new OID("1.3.6.1.4.1.9.9.311.1.1.2.1.15.1");
var = new OctetString("10.232.180.101");
trap.add(new VariableBinding(oid, var));
// 17. 1.3.6.1.4.1.9.9.311.1.1.2.1.16.1: 5858583a436f6d706f6e656e743d436f6d706f6e656e7431...
oid = new OID("1.3.6.1.4.1.9.9.311.1.1.2.1.16.1");
var = new OctetString("XXX:Component=Component1;ComponentClass-cclass1;YYY"); // Is this correct? Should it be "ComponentClass="?
trap.add(new VariableBinding(oid, var));
// 18. 1.3.6.1.4.1.9.9.311.1.1.2.1.17.1:
oid = new OID("1.3.6.1.4.1.9.9.311.1.1.2.1.17.1");
var = new Integer32(2);
trap.add(new VariableBinding(oid, var));
// 19. 1.3.6.1.4.1.9.9.311.1.1.2.1.18.1: 63656e416c61726d5365766572697479446566696e697469...
oid = new OID("1.3.6.1.4.1.9.9.311.1.1.2.1.18.1");
var = new OctetString("cenAlarmSeverityDefinition");
trap.add(new VariableBinding(oid, var));
// 20. 1.3.6.1.4.1.9.9.311.1.1.2.1.19.1:
oid = new OID("1.3.6.1.4.1.9.9.311.1.1.2.1.19.1");
var = new Integer32(1);
trap.add(new VariableBinding(oid, var));
// 21. 1.3.6.1.4.1.9.9.311.1.1.2.1.20.1: 31303030
oid = new OID("1.3.6.1.4.1.9.9.311.1.1.2.1.20.1");
var = new OctetString("1000");
trap.add(new VariableBinding(oid, var));
// 22. 1.3.6.1.4.1.9.9.311.1.1.2.1.21.1: 63656e557365724d65737361676531
oid = new OID("1.3.6.1.4.1.9.9.311.1.1.2.1.21.1");
var = new OctetString("cenUserMessage1");
trap.add(new VariableBinding(oid, var));
// 23. 1.3.6.1.4.1.9.9.311.1.1.2.1.22.1: 63656e557365724d65737361676532
oid = new OID("1.3.6.1.4.1.9.9.311.1.1.2.1.22.1");
var = new OctetString("cenUserMessage2");
trap.add(new VariableBinding(oid, var));
// 24. 1.3.6.1.4.1.9.9.311.1.1.2.1.23.1: 63656e557365724d65737361676533
oid = new OID("1.3.6.1.4.1.9.9.311.1.1.2.1.23.1");
var = new OctetString("cenUserMessage3");
trap.add(new VariableBinding(oid, var));
// 25. 1.3.6.1.4.1.9.9.311.1.1.2.1.24.1:
oid = new OID("1.3.6.1.4.1.9.9.311.1.1.2.1.24.1");
var = new Integer32(2);
trap.add(new VariableBinding(oid, var));
// 26. 1.3.6.1.4.1.9.9.311.1.1.2.1.25.1: 1
oid = new OID("1.3.6.1.4.1.9.9.311.1.1.2.1.25.1");
var = new Gauge32(1);
trap.add(new VariableBinding(oid, var));
// 27. 1.3.6.1.4.1.9.9.311.1.1.2.1.26.1: 63656e506172746974696f6e4e616d65
oid = new OID("1.3.6.1.4.1.9.9.311.1.1.2.1.26.1");
var = new OctetString("cenPartitionName");
trap.add(new VariableBinding(oid, var));
// 28. 1.3.6.1.4.1.9.9.311.1.1.2.1.27.1: 63656e437573746f6d65724964656e74696669636174696f...
oid = new OID("1.3.6.1.4.1.9.9.311.1.1.2.1.27.1");
var = new OctetString("cenCustomerIdentification");
trap.add(new VariableBinding(oid, var));
// 29. 1.3.6.1.4.1.9.9.311.1.1.2.1.28.1: 63656e437573746f6d65725265766973696f6e
oid = new OID("1.3.6.1.4.1.9.9.311.1.1.2.1.28.1");
var = new OctetString("cenCustomerRevision");
trap.add(new VariableBinding(oid, var));
// 30. 1.3.6.1.4.1.9.9.311.1.1.2.1.29.1: 63656e416c6572744944
oid = new OID("1.3.6.1.4.1.9.9.311.1.1.2.1.29.1");
var = new OctetString("cenAlertId");
trap.add(new VariableBinding(oid, var));
// 31. SNMP-COMMUNITY-MIB::snmpTrapAddress.0 (1.3.6.1.6.3.18.1.3.0): 127.0.0.1 (127.0.0.1)
oid = new OID(SnmpConstants.snmpTrapAddress);
var = new IpAddress("127.0.0.1");
trap.add(new VariableBinding(oid, var));
// Specify server to send the trap to.
Address targetaddress = new UdpAddress("10.232.181.31/162"); // Server listens for SNMP traps on port 162.
CommunityTarget target = new CommunityTarget();
target.setCommunity(new OctetString("public"));
target.setVersion(SnmpConstants.version2c);
target.setAddress(targetaddress);
// Send the trap.
lr.start_transaction("send_trap");
Snmp snmp = new Snmp(new DefaultUdpTransportMapping());
snmp.send(trap, target, null, null);
lr.end_transaction("send_trap", lr.AUTO);
return 0;
}//end of action
public int end() throws Throwable {
// Ignore this method.
return 0;
}//end of end
}
Success! Now that you have a working template (test it by running it from VuGen and doing a packet capture with Wireshark) you just have to modify the template to have the correct OIDs and value types, and replace your selected values with a parameter.
6 Comments
Comments are closed.



Hey Stu,
I’m guessing Wireshark couldn’t resolve the OID against its MIB templates. In my experience if the SNMP trap you send fails it falls back to being reported as UDP (because it couldn’t parse it in Wireshark) Maybe your hex data is borked …
In general though, any *decent* scripting language can easily accomplish this task. IMHO using LR to send snmp traps is overkill =)
e.g. in ruby
require ‘snmp’
include SNMP
manager = Manager.new(:Host => ‘localhost’)
varbind = VarBind.new(“1.3.6.1.2.1.1.5.0”, OctetString.new(“My System Name”))
manager.set(varbind)
manager.close
BTW, Jmeter can also do UDP requests with Google’s plugins =)
http://code.google.com/p/jmeter-plugins/wiki/UDPRequest?utm_source=jmeter&utm_medium=helplink&utm_campaign=UDPRequest
Or you could roll your own sampler in a similar fashion to above.
Nice work in showing us how it’s done with a Java vuser.
Cheers,
Tim
Hi Stuart,
“If anyone can explain this, I would love to hear from them.”
I’ve compared the Wireshark trace of the Loadrunner raw socket VUser with the Java VUser. The reason why Wireshark is interpreting the raw socket injection to be UDP and not SNMP is there’s some missing data at the end of the packet. Just add “\x00\x01” to buf0 in the Loadrunner raw socket script and Wireshark will start interpreting the injected packets as SNMP.
This begs the question why Wireshark interpreted the original Cisco Enterprise Policy Manager message to be SNMP if this data was missing. Maybe the data got accidentally sliced off during the dumping process?
It very nice to see the brief information that you have been provided about the the load test in the load runner. We are also have offering a product in doing the load testing, that you may reach us at, http://www.loadtracer.com/.
In case if you need of any performance testing services then you may reach us at: info@loadtracer.com.
You have third party tools that are as costly as loadrunner available for emulating SNMP devices. In this case, they take a copy of the SNMP database and create hundreds of virtual devices with different IP addresses. The virtual devices will respond to SNMP calls and can generate the traps as well.
Anyone happened to know what other open source tools we could use to simulate the SNMP traps?
snmpwalk and snmptrap