On June 19, HP announced in a press release that it had signed an agreement to acquire SPI Dynamics, a software company specialising in web security testing tools. The deal was finalised on August 1, and it is only now that theses new tools are reaching the wider pool of technical people (like me) at HP partner companies.
Purchasing SPI Dynamics nicely compliments HP’s November 2006 purchase of Mercury, who were best known for their defect management, functional test automation and performance testing tools. IBM has a similar portfolio in the software testing space, with the Rational products and their recent purchase of SPI’s main competitor, Watchfire, who created AppScan.
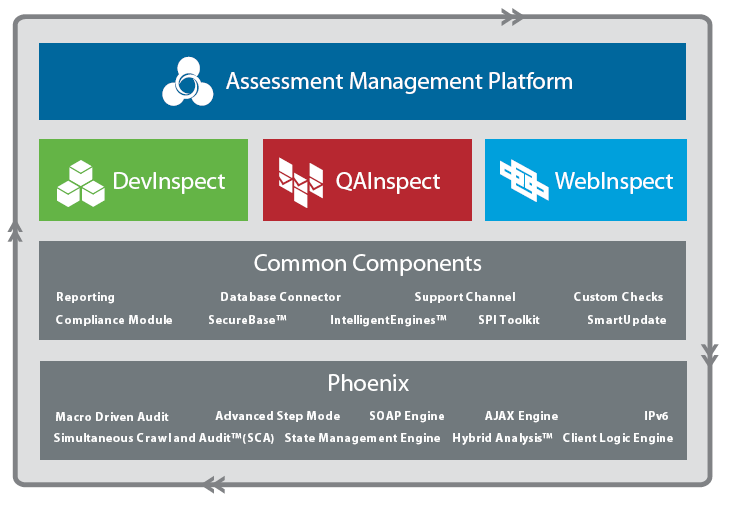
Here is a quick rundown of the SPI Dynamics product suite…
- Assessment Management Platform (AMP) is basically an “enterprisey” interface for their vulnerability scanning software. Manage and schedule regular scans across all of your company’s applications and report the results in a dashboard.
- WebInspect is their flagship product. DevInspect and QAInspect use the same engine, but WebInspect offers far more power than these tools. WebInspect will crawl a website and audit it for common classes of security defects such as SQL injection and cross-site scripting. A penetration tester can manually test for vulnerabilities with the application by viewing and modifying server requests.
- DevInspect is aimed at web application developers; it integrates with Visual Studio or Eclipse-based IDEs to perform analysis of Java and .NET source code for vulnerabilities. It will also audit the application from the web interface using the WebInspect engine.
- QAInspect is aimed at testers, and is pitched as a fully automated tool that testers can use without having any training or knowledge of security testing – push a button, scan the application, and get a report with detailed information about each vulnerability found. QAInspect integrates with both HP Quality Center and IBM Rational ClearCase.
- Web Application Security Services – SPI Dynamics also do service work. Presumably this will be absorbed into HP’s Professional Services group.
The 2007 SANS Top 20 Security Risks report noted that vulnerabilities in web applications account for almost half the total number of vulnerabilities being discovered in the past year, so there is clearly a huge number of opportunities to use this toolset to find problems before they are exposed to anyone with a web browser and a penchant for hacking web applications.
I’m looking forward to playing with WebInspect some more; and I’m planning on sharing some of the useful things I find on this website. If you’re interested in web security testing, you should subscribe to my RSS feed or check back soon.
One Comment
Comments are closed.



ooh nice shiny new blog Stu!
/subscribe
[Stuart’s Reply: Thanks Chris. Hope you enjoy my new blog.]